Threat intelligence is an alarming affair for most cybersecurity professionals. But what are some basics of threat intelligence that you need to know?
Cybersecurity professionals are well aware of the essentiality of threat intelligence strategies to safeguard organizations. The concerns become genuinely daunting with stricter laws around data privacy and impending cyber wars. So why not buckle up the defense by understanding the latest threats and vulnerabilities?
Threat Intelligence or better known as CTI(Cyber Threat intelligence) is a process to identify and mitigate potential or current cyber threats through intelligence demonstrated by platforms. Negligence on their importance can hamper an organization’s data and image.
Here we have a comprehensive guide on threat intelligence that can help you stay ahead of the curve-
Re-equipping with Tech
The discourse of traditional ways for threat intelligence is the initial theory. It paves the way through the quantity of data and sources to gather information on threats. But, managing and maintaining excel sheets is the real challenge for teams. Thanks to tech solutions – it takes away the pressure and bears more profitable results.
The systems and solutions chosen should be trustworthy. Only then professionals can glean valuable insights and take actionable measures. The platforms give top-class information based on the history of the organization. Such as the attacker’s information and the time it happened, the intent, and areas of compromise.
By integrating various group profiles, malware detection regulations, malware analytics, and actionable insights, the threat detection will be nearly real-time and accurate.
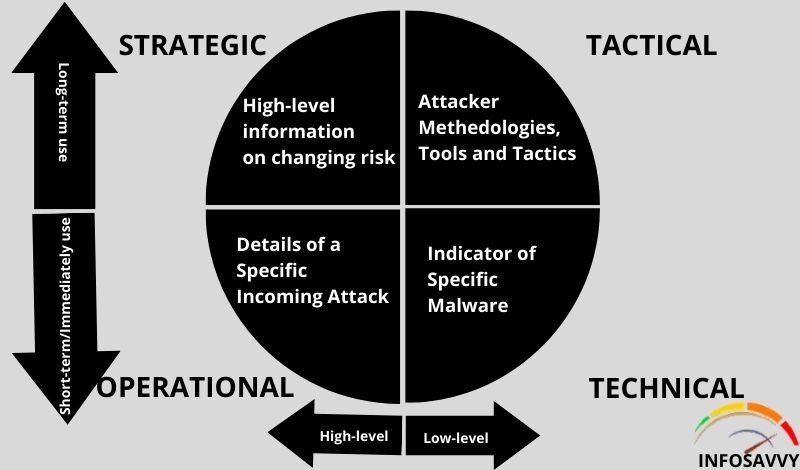
There are four main types of threat intelligence – Strategic, tactical, technical, and operational. Differing them into categories will give a definite way to approach cyber alerts. The necessary upgrade to the traditional methods will help teams detect and revert incidents faster.
Adding experts to an automated threat intelligence system who can design, build and operate will give the necessary human touch and aid you in staying ahead of the attackers.
Tips to make security asset
What is a firm’s greatest asset? It is its loyal and reliable employees. Hackers are highly adaptable to changing discourse of securities – making them almost immune to reinforced actions. The familiarity with cyber-attacks manner will turn your staff into security assets.
Organizations hold email marketing crucial to increasing reach and communication. Though efficient for communication purposes, it’s inevitable to distract cyber-criminals. Malicious links and trojans have cascading effects on an organization’s safety.
Though one of the austerest measures to mitigate risks is strong passwords, many fail to care. Multi-factor authentication systems are a great practice to ensure the right individual logging into the systems. In this way, you just don’t rely on passwords.
As remote work is the new normal, public WiFi is a risky gamble. They might not be end-to-end encrypted, putting the private data and corporate communication at menace.
Awareness-oriented training for figuring out suspicious emails is a great way to make your employees ready for what’s coming.
Ending Notes
Ideal threat intelligence practices should mitigate cyber risks and enhance business processes at the same time. Breaking down data silos and engaging stakeholders across organizational units will strengthen company intelligence.
Cybersecurity professionals must lead the way by making an effort to engage customers. Once they build a rapport by receiving relevant feedback, they can make better incident response strategies. At least 43% of businesses say they’ve had one or more security problems by software misconfiguration. So, the decision to invest modestly in such SaaS platforms becomes pivotal for leaders. By using the right systems, businesses configure problems. As the system keeps a note of every incident, the future tacklings become better. By upgrading to threat intelligence solutions, companies will get better problems and eventually render better solutions.
For more such updates and perspectives around Digital Innovation, IoT, Data Infrastructure, AI & Cybersecurity, go to AI-Techpark.com.

